As the cyber landscape evolves, security leaders are turning to proactive, community-driven solutions to uncover critical vulnerabilities before attackers do. Bug bounty programs have gone from niche experiments to essential components of modern security strategies. By tapping into a global network of ethical hackers, organizations can uncover critical vulnerabilities before malicious actors do—gaining real-world insight into their security posture. Should you launch one? What kind? How do you make sure it adds value instead of chaos? Whether you’re part of a lean startup or a seasoned security team at a large enterprise, this guide is built to give you clarity.
What Is a Bug Bounty Program?
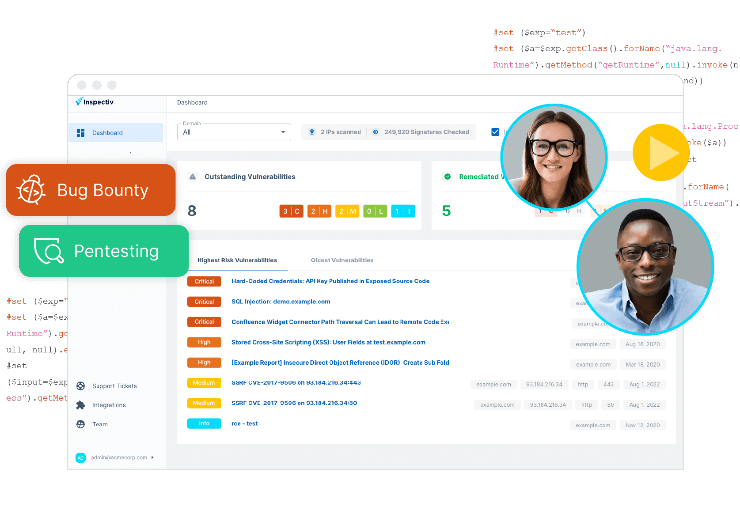
A Bug Bounty Program is a security initiative that invites ethical hackers (also know as security researchers) to identify and report vulnerabilities in an organization's assets. In return, these researchers receive financial rewards (or "bounties") based on the severity and impact of the issues they uncover. Unlike traditional security testing, bug bounty programs offer continuous, real-world coverage from a diverse pool of experts with varying skills and perspectives. These programs help organizations stay ahead of emerging threats while reinforcing a proactive security culture. When run effectively, they provide high-value insights without draining internal resources. But bounty programs typically fall into two categories:
- Public programs: Open to anyone in the ethical hacking community, inviting a broad range of researchers to test the environment. These programs can uncover a high volume of findings but may also require significant effort to manage noise and validate submissions.
- Private programs: Invite-only programs give organizations more control by limiting access to a curated group of trusted researchers. This approach often results in higher signal-to-noise rations and more manageable workflows, making it ideal of companies looking to test the waters or maintain tighter oversight.
Ultimately, whether you choose a public or private model, the goal remains the same: to strengthen your security posture through continuous, researcher-driven testing.
Why Companies Use Bug Bounty Programs
Organizations of all sizes are increasingly turning to bug bounty programs as a way to enhance their security posture, reduce risk, and uncover vulnerabilities that traditional testing may miss. One of the primary reasons companies adopt bug bounty programs is scale—by tapping into a global pool of researchers, companies benefit from diverse testing perspectives and techniques that mirror real-world attack scenarios. These programs also support continuous testing, helping teams identify issues in between scheduled security assessments or major product releases.
Bug Bounty programs complement other AppSec Testing strategies like penetration testing, dynamic application security testing (DAST), and vulnerability disclosure programs (VPDs). While pentests offer point-in-time, structured assessments and DAST automates the scanning of applications in real-time, bug bounty programs add an additional layer of human creativity and unpredictability. VDPs, on the other hand, provide a mechanism for responsible vulnerability intake—often without incentives. Often times researchers can find ways to chain multiple vulnerabilities together to perform a higher impact exploit that results in a greater compromise. When combined, these approaches create a layered, defense-in-depth model that increases coverage and helps organizations catch what others miss.
How to Start a Bug Bounty Program (the Right Way)
Bug bounty is more accessible than many teams realize—especially with the right support. While traditional programs may require heavy self-management, Inspectiv takes that burden off your team. Even small, understaffed security teams can successfully run a program with us. We handle researcher management, triage, and validation so you can focus on what matters most. Start by identifying your goals: Are you aiming to expand vulnerability coverage, meet compliance needs, or improve your security ROI? From there, define a scope that outlines which assets researchers can test and which are off-limits—transparency here helps reduce noise and build trust.
Next, decide whether a public or private model fits best with your risk profile and available resources. Many companies begin with a private program to maintain tighter control and ensure a smoother onboarding process for researchers. Over time, transitioning to a public program can help expand researcher participation and maximize coverage across your attack surface. Establish a fair and transparent reward structure that aligns bounty payouts with vulnerability severity. This not only incentivizes high-quality findings but also helps manage researcher expectations.
Managing a bug bounty program can quickly become overwhelming without the right support—especially when it comes to validating and prioritizing findings. That’s why many organizations choose to work with partners who specialize in reducing operational noise. With Inspectiv, you don’t have to sift through unverified reports or duplicate submissions. Every finding is reviewed, validated, and prioritized by our in-house experts before it ever reaches your team.
Penetration Testing vs. Bug Bounty Programs
Penetration testing and bug bounty programs are both valuable tools in an organization’s security arsenal—but they serve different purposes and offer different advantages. Pen tests are a structured, point-in-time assessment conducted by a limited number of professionals under a controlled scope. It provides a thorough snapshot of your security posture at a given moment, often used to satisfy compliance requirements or to test specific features before launch.
In contrast, bug bounty programs offer continuous, crowd-sourced testing from a diverse group of ethical hackers. They are ongoing by nature and leverage a variety of attacker mindsets, skill sets, and tools to uncover vulnerabilities that a traditional pentest might miss. Bug bounties are particularly effective at identifying business logic flaws, privilege escalation issues, and creative attack paths that automated tools and scripted tests can overlook.
For security leaders, the key isn’t choosing between the two—it’s understanding how and when to use each to maximize security outcomes. Think of pen testing like your scheduled annual physical, and bug bounty like real-time health monitoring. They work best together.
Why Bug Bounty Programs Fail (and How to Avoid It)
Bug bounty programs can be powerful—but only when executed with intention. Too often, programs fail because they’re launched without a clear purpose, defined scope, or internal alignment. This can result in an unmanageable flood of low-quality submissions, strained internal resources, and missed opportunities to uncover meaningful vulnerabilities.
Another major reason programs fall short is the operational burden they create. Without a dedicated process to vet, prioritize, and respond to incoming reports, even well-resourced teams can find themselves buried in noise. And when researchers don’t receive timely feedback or fair rewards, engagement drops off—weakening the very foundation of the program.
To avoid these pitfalls, successful programs are built on structure, communication, and support. That means defining clear goals and scope, setting researcher expectations, and ensuring your team is equipped to handle incoming findings efficiently.
Working with a partner like Inspectiv allows organizations to offload the noise. Every report is triaged and validated before reaching your team, so you're only focused on what’s real, impactful, and actionable. The result? A bug bounty program that drives value—not chaos. When done right, it’s not just another testing tool—it’s a force multiplier for your security strategy
What Makes a Good Bug Bounty Submission?
Not all bug reports are created equal. A high-quality bug bounty submission clearly outlines the issue, provides enough technical detail to reproduce it, and includes context on potential impact. For security teams, this clarity is essential—it speeds up triage, reduces back-and-forth with researchers, and accelerates time to remediation.
A good submission typically includes:
- A clear explanation of the vulnerability
- Steps to reproduce
- Evidence (screenshots, video, or payload)
- Impact assessment
- Suggested remediation
Submissions that follow these best practices are more likely to be validated quickly and rewarded appropriately. Inspectiv works closely with researchers to ensure all findings meet this standard before reaching your team.
Triage Matters: Why Real-Time Response is Key
In the world of bug bounty, speed matters. A vulnerability reported today could be exploited tomorrow—especially if it's left unreviewed or stuck in a backlog. That’s why real-time triage is critical. The faster a submission is reviewed, validated, and prioritized, the faster your team can respond, mitigate risk, and maintain trust with both researchers and stakeholders.
Delays in triage not only slow down remediation efforts, but can also damage your program’s reputation. Researchers are less likely to stay engaged if they feel their work isn’t acknowledged or acted upon quickly. And internally, a backlog of unreviewed reports can overwhelm teams and dilute focus from the most critical issues.
Effective triage is more than just reviewing reports—it’s about filtering signal from noise, eliminating duplicates, assessing severity, and ensuring only high-impact findings reach your team. That’s why Inspectiv integrates real-time triage with human expertise, so you’re never caught off guard and never waste cycles chasing false positives.
Common Vulnerabilities in 2025
As threats continue to evolve, so do the types of vulnerabilities researchers uncover through bug bounty programs. In 2025, many of the most common—and dangerous—security flaws stem from the rapid adoption of cloud-native architectures, AI-driven applications, and modern development frameworks.
Here are some of the top vulnerabilities organizations should be watching for this year:
- Cross-site scripting (XSS)
- Broken access controls
- Exposed sensitive data: API keys of PII
- Insecure direct object references (IDOR)
- SQL injection
Modern web applications are more complex than ever. Bug bounty programs are uniquely positioned to surface these issues—especially those that automated scanners and traditional tests may miss.
Are Bug Bounty Programs Worth It?
For many organizations, the idea of opening up their environment to external researchers can feel risky or resource-intensive. But when structured and managed effectively, bug bounty programs deliver clear, measurable value—and can significantly strengthen your overall security posture.
The ROI of a bug bounty program comes down to a few key factors: the quality of findings, the efficiency of your triage process, and the alignment with your broader security goals. Unlike traditional testing models that operate on fixed timelines and fees, bug bounty programs reward impact. You only pay for valid, actionable vulnerabilities, which makes it easier to control costs and focus on results.
Bug bounty programs also provide unique advantages that are difficult to replicate with internal resources alone. The global researcher community brings diverse perspectives, tools, and techniques—often uncovering creative attack paths that in-house teams or automated tools may miss. They also provide continuous coverage, helping you stay protected between pentest cycles or major product releases.
Of course, success isn’t guaranteed. Programs that lack scope, structure, or internal support often fall short. But when backed by a clear strategy and strong operational support—like expert triage and researcher management—bug bounty programs become a scalable, high-impact layer of modern security.
So are they worth it? For organizations committed to proactive, real-world defense: absolutely.
FAQs
Are bug bounty programs legal?
Yes. With a properly defined scope and disclosure policy, they provide a safe and legal way for researchers to test your systems.
Do bug bounty programs work?
When structured and supported correctly, they are highly effective at uncovering issues traditional testing might miss.
What software is used for bug bounty?
Most programs use platforms to manage researcher submissions, triage, and payouts. Inspectiv offers a full solution with expert validation built in.
Who can perform security research on a bug bounty program?
Many programs welcome all experience levels, but rewards are based on report quality and impact.
Why Inspectiv?
Launching a bug bounty program is one thing—running it efficiently is another. At Inspectiv, we specialize in helping security teams unlock the full value of bug bounty testing without the operational burden. As a fully managed bug bounty platform, we assume the heavy lifting that traditional platforms often leave to internal teams—from triage and validation to researcher engagement and reporting. Our Bug Bounty as a Service offering is designed for teams that want high-impact results without getting buried in noise or stretched thin on resources.
We don’t just connect you with researchers—we act as your frontline. Every submission is triaged and validated by our in-house security experts before it ever hits your queue. That means no duplicates, no false positives, and no chasing down low-quality reports. Just clear, actionable findings you can trust.
Inspectiv works as an extension of your team, aligning our work to your risk priorities, compliance requirements, and internal processes. Whether you're scaling a program from scratch or maturing an existing one, we help you drive meaningful outcomes—without distracting your engineers or overwhelming your resources.
With Inspectiv, you get the power of the crowd and the precision of expert validation—all in one continuous testing solution. If you’re looking for more than a dashboard, we’d love to talk.