Platform
Manage and remediate vulnerabilities with real-time dashboards, integrations, and expert validation.
Platform
Manage and remediate vulnerabilities with real-time dashboards, integrations, and expert validation.
See Inspectiv in Action!
Schedule a live demo to see how our platform helps you manage vulnerabilities, reduce noise, and stay compliant.

See Inspectiv in Action!
Schedule a live demo to see how our platform helps you manage vulnerabilities, reduce noise, and stay compliant.
Integrated Bug Bounty, Pentesting, DAST, and VDP

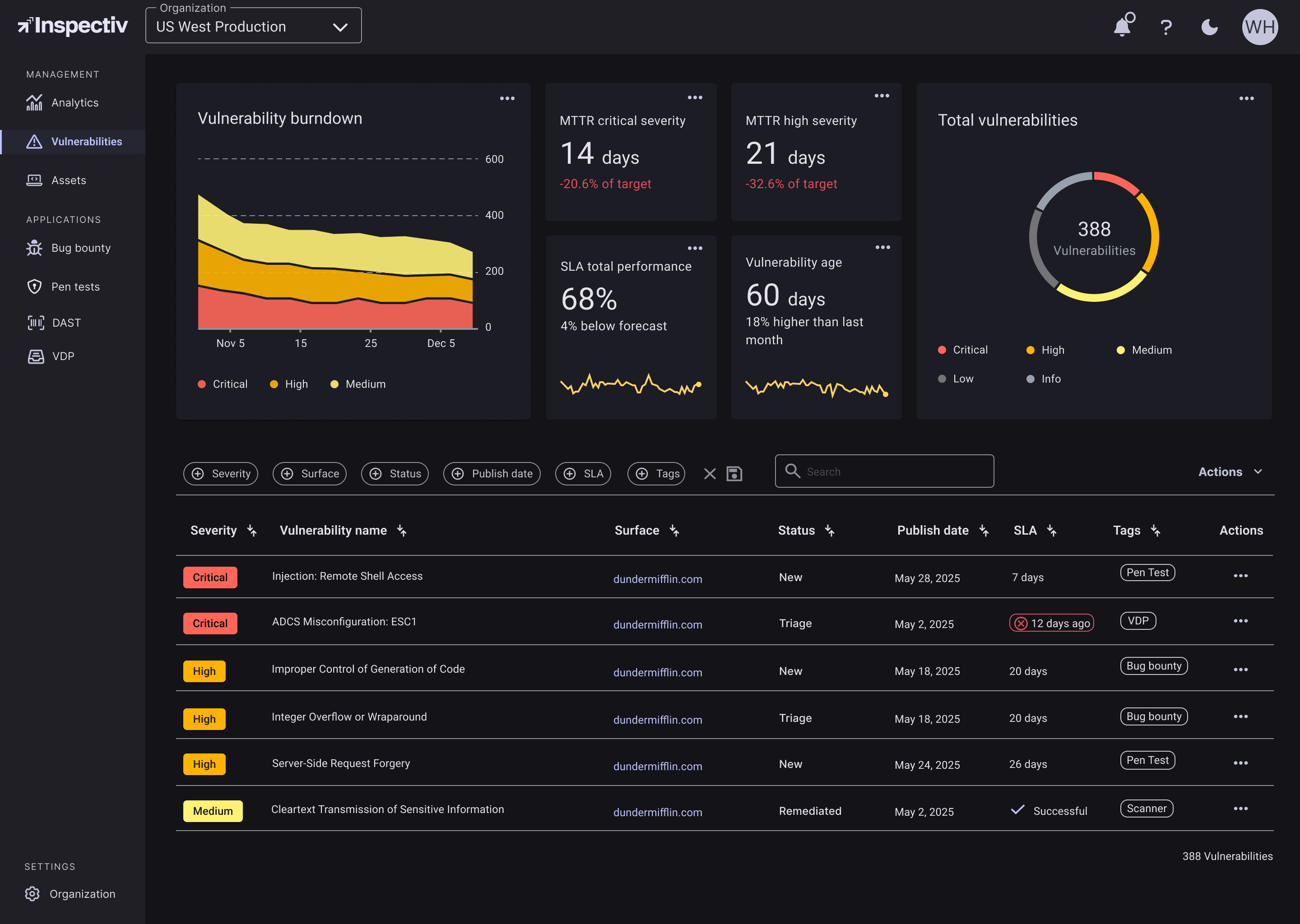
Inspectiv combines Bug Bounty, Pentesting, DAST, and VDP into a single, integrated solution that works the way your team does. All findings flow into a single dashboard, giving you a clear, centralized view of your risk landscape without having to juggle between fragmented tools and vendors. Every submission is validated by our triage team, helping you cut through the noise and focus on the vulnerabilities that matter. Whether it’s a high-impact pentest finding, a DAST-detected runtime issue, or a responsible disclosure through VDP, Inspectiv connects the dots and delivers the context your team needs to respond with speed and confidence.
Inspectiv integrates into the tools your team already uses, such as Jira, Slack, APIs and webhooks, ensuring validated findings show up where work is happening, not buried in dashboards. Real-time Slack alerts and webhook support ensure critical issues reach the right people fast. By filtering out noise and surfacing only high-impact vulnerabilities, we help teams focus on what matters, stay compliant, and simplify reporting. Whether you're scaling fast, launching new features, or working with limited resources, Inspectiv helps you move quickly without compromising security.


Inspectiv acts as an extension of your security team, bringing expert support, continuous testing, and clear guidance without adding more to your plate. We manage the end-to-end process across Bug Bounty, Pentesting, DAST, and VDP, so you don’t have to juggle vendors or triage every alert. Every submission is replicated, validated, and retested as needed. We handle researcher communication, streamline reporting, and integrate directly with your existing tools. You get high-impact findings, fewer false positives, and a faster path to resolution, delivered in a way that works with your team, not against it.
Sr. Principal Application Security Engineer
ServiceTitan
Ready to level up your AppSec program? Book a personalized demo to see how Inspectiv helps you uncover real risks, streamline workflows, and scale your security program through one unified platform designed to operate the way your team does.
