Modern organizations rely on software to power operations, connect teams, and deliver services across the web. As Application Programming Interfaces (APIs) and web technologies continue to expand, so do attack surfaces, introducing new vulnerabilities. Each year, thousands of these vulnerabilities are discovered—many only after significant financial and reputational damage has occurred. Data breaches from misconfigurations and software flaws cause billions in losses and expose sensitive credentials, fueling further security risks.
With each organization’s unique applications and security needs, safeguarding these complex environments presents distinct challenges. To address these, teams turn to two primary methods of application security testing—Static (SAST) and Dynamic (DAST)—each offering different advantages to enhance security posture.
SAST: Uncovering Vulnerabilities at the Code Level
Static Application Security Testing (SAST) is a crucial cybersecurity methodology focused on analyzing the source code of applications to identify security vulnerabilities early in the development lifecycle. Unlike dynamic testing, which assesses applications in a running state, SAST inspects the code itself in order to determine vulnerabilities as they arise. SAST can detect common vulnerabilities which hackers weaponize against unsuspecting code, such as Buffer overflows, SQL injections, and input validation attacks, which can cause attackers to execute malicious arbitrary code, as well as Denial of Service (DoS) attacks, which can paralyze a device or entire network. Other attacks which manipulate access or variables, such as Path Traversal or Cross-site request forgery (CSRF), can be detected with this method.
By allowing teams to find exploitable vulnerabilities early in the development process, SAST offers valuable insights into data flows, syntax and relationships between classes in software code as well as licensing requirements. The earlier stage testing allows developers to receive feedback in real-time, allowing the changes to be made as part of the Software Development Lifecycle (SDLC). Additionally, SAST tests can also be run in tandem with web applications and APIs which software needs for workflows to pinpoint root causes.
However, SAST has some limitations in visibility compared to Dynamic Application Security Testing (DAST). It often relies on predefined rulesets, which can restrict its ability to detect new or evolving vulnerabilities in source code. Moreover, identifying runtime errors remains challenging when using only SAST, as it primarily focuses on static code analysis.
DAST: A Comprehensive, Tailored Solution
Dynamic Application Security Testing (DAST) is a method of security testing that focuses on analyzing applications in their running state to identify vulnerabilities that may only emerge during actual use. Unlike Static Application Security Testing (SAST), which inspects the underlying code, DAST simulates real-world attacks and interactions to uncover security flaws in an application’s interfaces, inputs, and outputs. It targets everything from encryption processes and authentication errors to OS-specific vulnerabilities. By testing applications as they operate, DAST provides comprehensive coverage, detecting issues that could be exploited by attackers in a live environment. This method is especially effective at identifying security weaknesses that arise from application behavior, configuration settings, or complex workflows.
Dynamic Application Security Testing (DAST) is a more comprehensive option for teams who view security as an essential foundation to their organization. Although it typically occurs later in the development process, DAST offers critical insights to ensure applications remain robust and secure once deployed. A successful DAST deployment relies on full access to the application and its operating environment, from HTTP Headers to authentication processes to network traffic flows while identifying any code dependencies. Effective DAST testing involves simulating real-world attack scenarios such as Cross-site Scripting (XSS), SQL injection, web crawling against organization networks, and excessive input handling. Additionally, DAST rigorously examines authentication systems, credential security, and the Document Object Model (DOM) to ensure comprehensive protection and readiness for deployment.
Maximizing Security: The Role of SAST, DAST, and Inspectiv’s Solutions
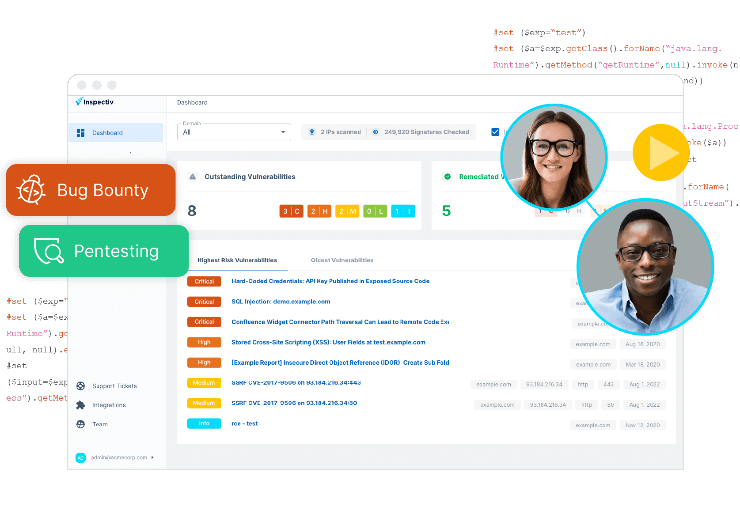
Both testing methodologies offer unique strengths and challenges for application security. While SAST excels at identifying vulnerabilities early in the code development process, DAST simulates real-world attack scenarios on running applications, providing a comprehensive view of potential security weaknesses that could be exploited once the application is deployed. Although DAST often demands more time and resources, its ability to detect runtime vulnerabilities and simulate real-world threats is crucial for protecting organizations from devastating breaches and reputational damage. For many organizations, executing a full DAST lifecycle can be complex and resource-intensive. This is where expert solutions, like Inspectiv’s DAST, become invaluable.
Developed based on industry-leading OWASP standards, Inspectiv's DAST seamlessly integrates with vulnerability management programs and seamlessly integrates into vulnerability management while offering cutting-edge bug bounty and pentesting services to provide full-spectrum coverage for your organization’s code base. DAST emulates penetration testing methodologies in a programmatic way, giving you fast results in a unified platform that serves as an essential pillar to DevSecOps workflows.