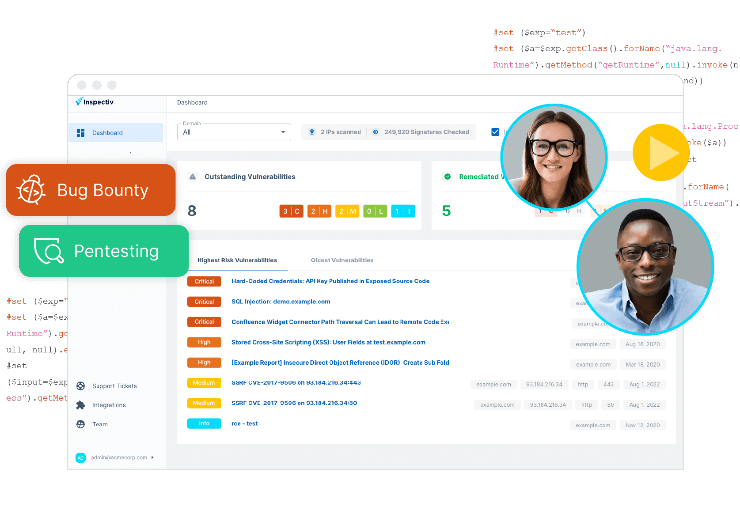
Bug bounty programs have become a popular method for organizations to bolster their cybersecurity defenses by incentivizing external ethical hackers to uncover vulnerabilities in their applications and systems. However, one common challenge is the potential of incoming researcher inquiries at a high-volume, often perceived as "noise", and having to manage that communication.
Challenges of Traditional Bug Bounty Programs
Traditional bug bounty programs, while effective in rooting out vulnerabilities, have some important downsides. If not managed properly, these actually create more work for already busy teams.
- The first is the “signal to noise” ratio for the huge volume of reports that teams have to evaluate and act on. When these programs open to the public, plenty of ethical hackers jump onboard, each keen on identifying vulnerabilities and claiming the associated rewards. Theoretically, this should lead to the discovery of more problems. The problem isn’t the volume of submissions, but rather the value.
The influx of such low-priority vulnerabilities can swamp an organization, leading to a phenomenon referred to as "noise." This noise can have several undesirable consequences for a company, like creating an additional administrative burden from reviewing each vulnerability submission, as well as how resource-intensive the review process is to complete. The noise can also obscure the significant, high-risk vulnerability signals that deserve immediate attention.
- The second downside is the huge number of relationships that have to be managed, from finding and onboarding researchers to managing payments. Again, if the goal is to help the security team get more time to focus on threat hunting, traditional bug bounty programs can be counterproductive.
Luckily, for businesses who want high level external expertise that doesn’t add complexity to their workloads, Inspectiv has a solution.
Inspectiv’s Solution to Bug Bounty Noise
Inspectiv helps development teams build secure, modern software by giving them access to experts who are focused on your biggest risks. The result is a better product for customers, with less intervention from security teams. This means your critical security experts don’t spend time analyzing reports looking for insights, or chasing researchers for payment details.
We do this by working to understand your business and tech priorities, and assembling a specialized set of researchers to help you get there, via carefully controlled private engagement.
Additionally, Inspectiv helps streamline the communication process with researchers, effectively managing interactions to maintain focus and efficiency.
This careful control ensures organizations don't lose sight of the primary objective—identifying and resolving only the significant vulnerabilities. The platform is engineered to prioritize vulnerabilities according to their risk. This means organizations can breathe easy, knowing that their attention will be drawn to the more pressing issues that could compromise their system's security.
Customizable Scope and Scale With Inspectiv
With Inspectiv, organizations have the benefit of flexibility. You can initially launch a small, easily manageable program and have the ability to expand based on your organization's security needs and available resources. Subsidiaries can even introduce independent programs, resulting in tailored security solutions that don't overwhelm the parent company's resources.
With such customization, every scale of business—from startups to multinational corporations—can leverage the bug bounty benefits only from Inspectiv.
Practical Ways Inspectiv Can Help
Inspectiv provides a comprehensive suite of analytics, equipping organizations with valuable insights into their vulnerability landscape. This information can be used to inform strategic decision-making and allocate resources more effectively. The platform is also designed to seamlessly integrate with existing processes and tools, minimizing disruptive changes to operations.
With Inspectiv, organizations can also access real-time data, ensuring that they are constantly updated on any new vulnerabilities found. This proactiveness allows rapid response to potential issues before they become significant threats, further enhancing the organization's cybersecurity.
Apart from sophisticated analytics, Inspectiv also offers a guided approach to vulnerability submission. This allows researchers to provide detailed, standardized reports of their findings, making it easier for organizations to make sense of the data. Inspectiv also employs its team of experienced vulnerability analysts who critically review each submission, ensuring that only support on all vulnerabilities. These layers of review and services save organizations valuable time and resources and showcases the accuracy that customers can appreciate.
Implement Inspectiv for Better Bug Bounties
Inspectiv is the clear way to go when it comes to getting the most out of your bug bounty programs. With Inspectiv, your bug bounties will be more efficient, effective, and able to target specific, dangerous vulnerabilities by reducing the noise that otherwise clogs up your review. Organizations can stay focussed on the most critical vulnerabilities, ensuring optimal use of resources while also getting access to experts who keep your software secure today and tomorrow.
If you’re an organization looking to streamline your cybersecurity efforts, consider giving Inspectiv a try. You'll notice a clear difference in how you manage and respond to vulnerabilities, elevating your overall cybersecurity posture. Learn more about Inspectiv's offerings or book a demo session on our website today.