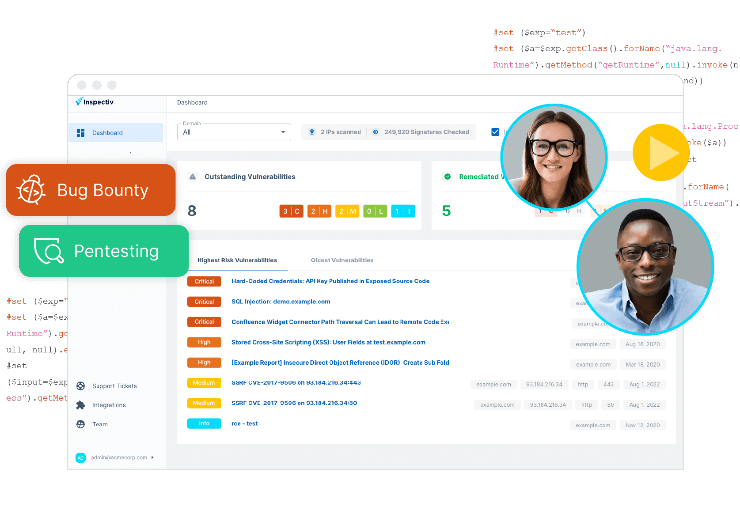
Bug Bounty programs have become a crucial part of cybersecurity strategies for organizations worldwide. As the digital landscape evolves, the importance of identifying and patching vulnerabilities before they can be exploited by malicious actors has never been more critical.
According to Bug Bounty industry statistics, “the bug bounty market is valued at $223.1 million in 2020, which will grow to $5,465.5 million in 2027. The rise of AI and the mainstreaming of cybersecurity will continue to shape the bug bounty industry, as well as the increasing importance of transparency in vulnerability disclosures.”
Understanding important choices
As organizations look to employ bug bounty services, they face some important choices. While traditional bug bounty programs remain enormously popular, new alternatives may actually give most businesses a better option.
This blog looks at what Bug Bounty programs are, how they work, the benefits they offer, and how organizations can integrate them into their cybersecurity strategies. It also looks at how Inspectiv’s unique approach might be a better alternative than other options. Whether you are new to Bug Bounty or looking to enhance your existing program, get valuable insights into the world of ethical hacking and vulnerability disclosure.
How Bug Bounty Programs Work
The operation of Bug Bounty programs is primarily based on the collaboration of cybersecurity-minded individuals who are incentivized by rewards to find and report software vulnerabilities. Companies or organizations typically set up a Bug Bounty program, laying out the rules, scope, and bounty rewards for identifying each type of bug.
Participants, known as bug bounty hunters, then use their cybersecurity skills to find and report software bugs within the defined program scope. Upon confirming a reported bug, the organization rewards the bug bounty hunter based on the severity and potential impact of the discovered vulnerability.
Role of Bug Bounty Hunters
Bug Bounty hunters are the heroes and protagonists of this cybersecurity initiative. Their deep expertise in web security, application security, infrastructure security, and other areas enables them to identify security flaws in target systems that may otherwise go unnoticed. Bounty hunters essentially act as ethical hackers, using their skills to improve security rather than exploit vulnerabilities. Their goal is aligned with the organization's objective—to make the digital environment more secure.
Traditional Payout Methods vs. Inspectiv's Fixed Cost Model
One downside of traditional bug bounty programs is cost uncertainty. These programs rely on a risk-laden payout structure that directly ties bounty payouts to vulnerability severity. As a result, they often face the unpredictability of researcher payouts and the risk of running out of funds. The constant budget requests can also create internal conflicts and concerns.
On the other hand, Inspectiv's pricing model presents a more predictable budgeting approach with its Bug Bounty as a Service. It decouples payout from vulnerability severity, offering fixed payments for each bug discovered. This model benefits both organizations—which can budget their programs effectively—and bug hunters, who receive consistent rewards.
Benefits of Bug Bounty Programs
Bug Bounty programs are not just about finding vulnerabilities; they offer numerous other benefits to organizations that employ them. Some of these advantages include:
Bug Bounty programs are not just about finding vulnerabilities; they offer numerous other benefits to organizations that employ them. Some of these advantages include:
Enhanced and Continuous Security Testing
Unlike standard security audits or penetration tests, Bug Bounty programs offer continuous vulnerability detection. They engage a community of talented hackers who persistently scrutinize the software to find potential gaps. This continuous evaluation approach ensures timely detection and remediation of vulnerabilities, providing a higher level of security for the organization's systems.
Cost-Effective Vulnerability Identification
Utilizing a Bug Bounty program can significantly reduce the cost of vulnerability identification. Instead of funding an extensive in-house testing team or spending on expensive security audits, organizations can leverage a wide network of independent researchers. As a result, companies only pay when a valid security flaw is discovered, making Bug Bounty a cost-effective solution for vulnerability identification. Payments can vary from small to large depending on the size of the vulnerability found. Making sure that there is an ample amount of budgeting set aside is recommended due to the variability of cost.
Access to Top Talent of Security Researchers
By running a Bug Bounty program, organizations have the ability to tap into a community of skilled security researchers from around the world. These researchers bring a diverse range of skills, expertise, and perspectives to the hunt for bugs, which can lead to better identification and mitigation of security risks.
Create Consumer Confidence in Your Security Posture
Having a Bug Bounty program in place signals to customers and stakeholders that the organization prioritizes cybersecurity. It shows that you’re proactive about finding and patching vulnerabilities. This can boost consumer confidence in the organization's security posture and add to enhancing its reputation in the market.
Integrating Bug Bounty Programs into your Cybersecurity Strategy
Implementing a successful Bug Bounty program requires a deliberate strategy. It is crucial to define the scope of the program clearly, communicate the guidelines effectively to the bug bounty hunters, and ensure a quick turnaround time for bug verification and payout. Also, maintaining transparency and keeping open channels of communication with the researchers can help build a healthy relationship and encourage more participation.
Considerations for Organizations
Organizations looking to implement a Bug Bounty program should consider their security maturity, budget allocation for the program, and the types of vulnerabilities they want to target. It's also important to have a dedicated team to manage the program and handle the reported vulnerabilities efficiently.
The challenge, even for large organizations, is finding the dollars and talent to support the effort. Financially speaking, traditional bug programs often require escrow funding to ensure researchers get paid for their efforts. But as researchers work, these funds need to be continuously replenished, making more work for finance and operations in the process.
These programs can also overwhelm team members with lots of low quality findings, all which need to be managed and tracked. Security researchers are typically concerned with finding problems not solutions, so it’s up to IT and security to mitigate.
In-house Bug Bounty Programs vs. Platform-Based Bug Bounty Programs
Comparing in-house bug bounty programs to platform-based ones, both have their merits. In-house programs grant more control over the process. You can tailor the program to your specific needs and directly manage relationships with bug hunters. However, it can be resource-intensive and require a higher level of expertise.
On the other hand, platform-based bug bounty programs offer robust infrastructure, a wide pool of researchers, and extensive support services. They handle much of the operational burden, allowing your organization to focus on resolving reported vulnerabilities.
Bug Bounty Program Management
Before implementing a bug bounty program, it’s best to learn how to manage one.
Setting Scope and Rewards
Defining the scope accurately is crucial in Bug Bounty program management. It provides clarity to the bug bounty researchers about the areas of the programs they should focus on. Organizations also need to set the reward structure, which can vary depending on the severity of the bug discovered. However, it’s important to keep the rewards competitive to attract and incentivize talented researchers.
Handling Reported Vulnerabilities
Once bugs are reported, organizations should validate them promptly. If verified, the bugs should be fixed as soon as possible to prevent potential exploitation. This requires a well-coordinated effort from the organization’s security team, working alongside security and compliance teams to make sure errors get fixed and the process gets documented.
A smarter alternative
Inspectiv helps organizations reduce time spent managing bug bounty programs and their findings. We work with teams to better understand their software environment. This ensures we always bring the right expertise to the challenge, including cloud and other advanced software skills you can’t always find through traditional methods.
This means you’ll not only get higher quality findings across your complete software stack, you’ll spend less time mitigating the vulnerabilities themselves. Each finding comes with a video that can be sent directly to a developer or engineer, giving them the knowledge they need to mitigate the problem without much intervention from IT or security. Inspectiv also manages the payouts after findings, another time-consuming task.
Future Trends in Bug Bounty Programs
Bug Bounty programs are evolving as cyber threats become increasingly sophisticated. As the Bug Bounty industry statistics state, “Websites are the most attacked vendor; [hence there has been] a 151% increase in reports from 2021… More and more companies are moving towards Bug [Bounty programs] for their overall security.”
More Companies Adopting Bug Bounty Programs Recently
Bug Bounty programs are not limited to tech giants. Many businesses across different sectors are launching their initiatives, demonstrating the growing importance of these programs in the cybersecurity landscape. In 2023, we saw Google extend its program to cover generative AI security concerns, Swisstronik provide rewards of up to $31,000 for each identified bug, and SquareX employ bug hunters to assess the security of its browser-based cybersecurity product through hacking tests. Even cybersecurity firms like Malwarebytes are getting in on the action, with a program offering rewards from $50 to $2,000 for valid bug reports.
Potential Impact on the Cybersecurity Landscape
As more organizations adopt Bug Bounty programs, the cybersecurity landscape is likely to see a significant shift. These programs may pave the way for more responsible vulnerability disclosure, better security for digital products, and potential mitigation of cyber threats. But this will all require a lot more help from security researchers.
Bug Bounty as a Service (BBaaS) is a natural evolution of this need. Organizations will need access to broader and broader skill sets, including experts solely focused on watching for and understanding emerging threats. At the same time, they’ll also need to carefully preserve budget, especially smaller orgs.
BBaaS gives them the ideal balance of economy and efficiency. As with all things “as a service”. BBaaS reduces costs, ensures you always have the resources you need when you need them, and reduces hours left to manage the whole process, especially when you can integrate findings into your own systems.
Start a Bug Bounty Program for Your Business
Bug Bounty Programs are proving to be an essential element in the cybersecurity ecosystem. By incentivizing skilled researchers to find and report vulnerabilities, they enable organizations to enhance their security posture significantly.
Organizations that have not yet considered this approach should contemplate how a Bug Bounty program could strengthen their cybersecurity strategy. With the ongoing increase in cyber threats, there is no better time than now to start a Bug Bounty program. When paired with regular penetration testing, it provides core defenses across your dev lifecycle.
But bug bounty programs are a lot of work. You’ll need to build a funding mechanism, find a platform for managing reporting, and figure out how to tap into the right network of researchers. Once the program starts, you’ll need to assign staff to manage the flow of findings, questions, payments, and everything else, in addition to having to track down specialized expertise when it’s required.
For organizations who can’t run a program in-house, it’s time to consider provider alternatives. BBaaS providers combine the best attributes of traditional bug bounty programs with a cost model that gives leaders transparency and predictability. They also empower IT and security teams, saving them time mitigating vulnerabilities and managing the program itself. This is why organizations trust the Inspectiv solution: deeper vulnerabilities coverage that takes less time and money to accomplish.