Bug Bounty Program
Get 24/7 expert-led testing, trusted triage support, actionable results, and zero overhead.


Modern Bug Bounty Testing Without the Chaos
Traditional bug bounty programs are noisy, unpredictable, and hard to manage. Inspectiv changes that. Our managed program pairs top-tier researchers with human-vetted vulnerability findings to surface only validated, high-impact findings. Every submission is replicated before it reaches your developers, and every fix is re-tested. No guesswork. No wasted time. Just continuous, scalable security testing backed by flat-fee pricing you can trust.
Product Benefits
Continuous Risk Discovery
Get 24/7 vulnerability testing across web, mobile, and APIs to help you stay ahead of threats with always-on coverage that complements your existing security strategy.
Validated, Actionable Results
Every finding is reviewed and replicated by our triage team before reaching your developers, so you can prioritize confidently and eliminate the noise of false positives.
Flat-Fee, Predictable Pricing
No escrow, no surprises. Our transparent subscription pricing includes all researcher payouts and program management, making it easy to budget and scale.

Seamless Program Management
Inspectiv handles all researcher communication, coordination, and retesting, offloading operational overhead and freeing up your team to focus on remediation.
What is Bug Bounty?
A bug bounty program is a proactive approach to security testing that invites ethical hackers, also known as security researchers, to uncover and report vulnerabilities in your applications, APIs, and infrastructure. In return, researchers are rewarded with bounties based on the severity and impact of their findings. It’s a powerful way to extend your coverage and discover issues that traditional testing often misses. Inspectiv supports both private and public Bug Bounty programs, giving you the flexibility based on your risk tolerance and program maturity. Many teams start with a private program to maintain tighter control, then expand to a public program for broader attack surface coverage and deeper insights. For teams juggling compliance requirements, limited bandwidth, and expanding attack surfaces, Inspectiv makes bug bounty manageable. We handle all researcher communications, replicate every submission, validate each finding for accuracy, and provide clear remediation guidance. The result? Continuous security insights without the chaos delivered through a streamlined platform and supported by transparent, flat-fee pricing.
Why Choose Inspectiv for your Bug Bounty Program?
Traditional bug bounty platforms can create more work than they solve by flooding your team with noisy reports, inconsistent researcher quality, and unpredictable costs. Inspectiv simplifies the process with a fully managed approach that puts control, clarity, and confidence back in your hands.With Inspectiv, you get continuous vulnerability discovery without the operational burden. Our triage team validates and replicates every submission, so your developers only see what matters. We handle all researcher communications, payouts, and retesting, freeing your internal team to focus on fixing issues, not managing logistics.And with flat-fee pricing, there’s no guesswork. You know exactly what you’re paying with no escrow, no bounty surprises. Inspectiv turns bug bounty into a reliable, scalable layer of your AppSec strategy, helping you find more critical vulnerabilities, reduce risk faster, and scale securely.
Highly-Skilled Security Researchers
Inspectiv's bug bounty programs are powered by a global community of experienced security researchers who specialize in identifying real-world vulnerabilities across modern environments. From web applications and APIs, these researchers continuously test your systems, serving as an always-on extension of your security team and uncovering risks that automated tools often miss. Our triage team creates structured scopes with clear rules of engagement, managing all communication from scope management to payouts, while our unified platform gives security teams complete visibility into vulnerability trends, testing activity, and remediation progress across their entire security program.
All researcher interactions are handled by Inspectiv behind the scenes, so you can take full advantage of a thriving security community without adding extra work to your team.
Get a Demo
Vulnerability Reports You Can Trust
Inspectiv goes beyond typical bug bounty triage. Every vulnerability is reviewed, validated, and replicated by our expert team. You get the context and clarity your developers need for successful threat remediation.
Get a Demo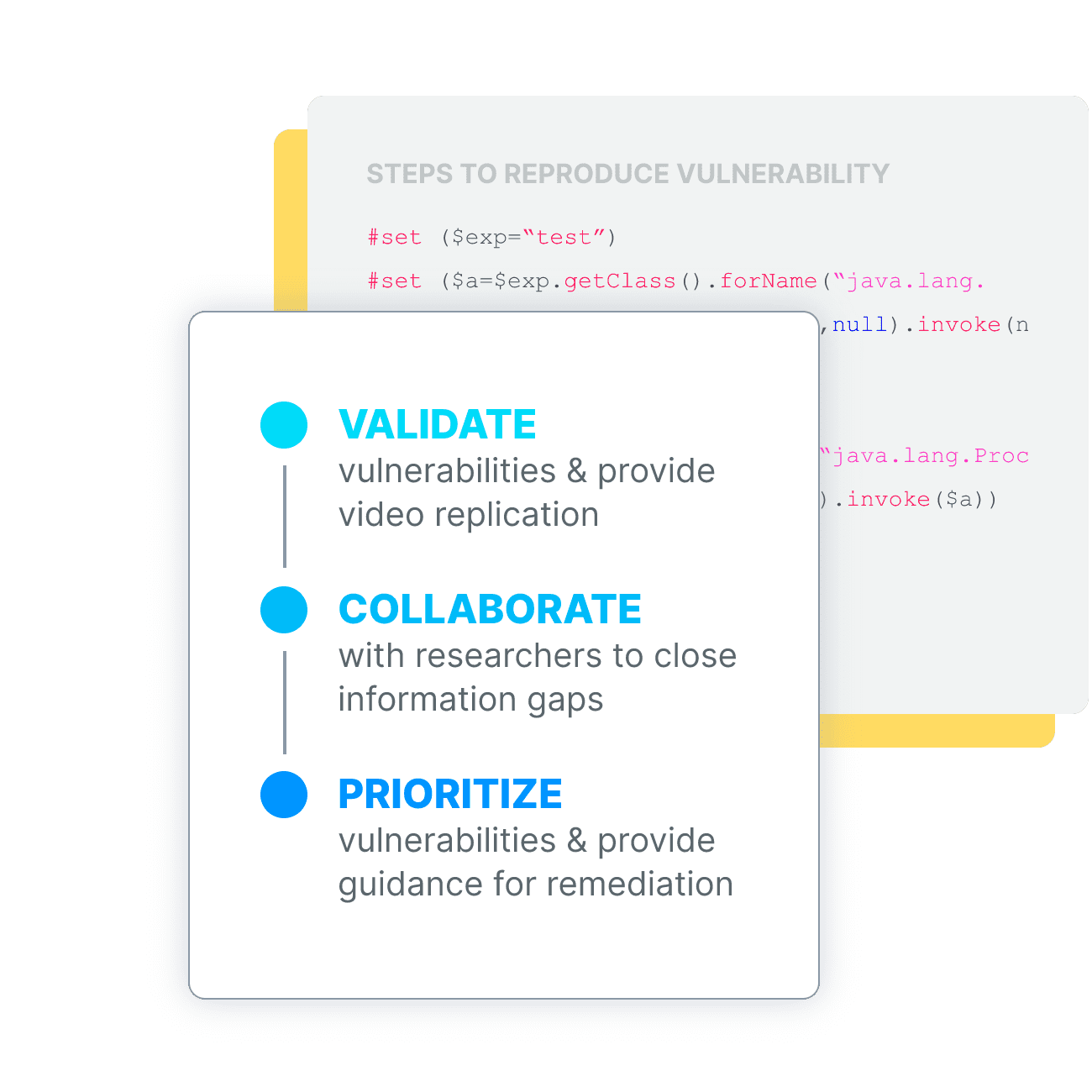
Predictable Bug Bounty Program Pricing
Inspectiv’s flat-fee subscription model means you know exactly what to budget today and into the future as you scale up your bug bounty programs. We manage all payouts and offer a range of incentives designed to attract and rotate researchers, so your team can stay focused on innovation and you budget with confidence.
Get a Demo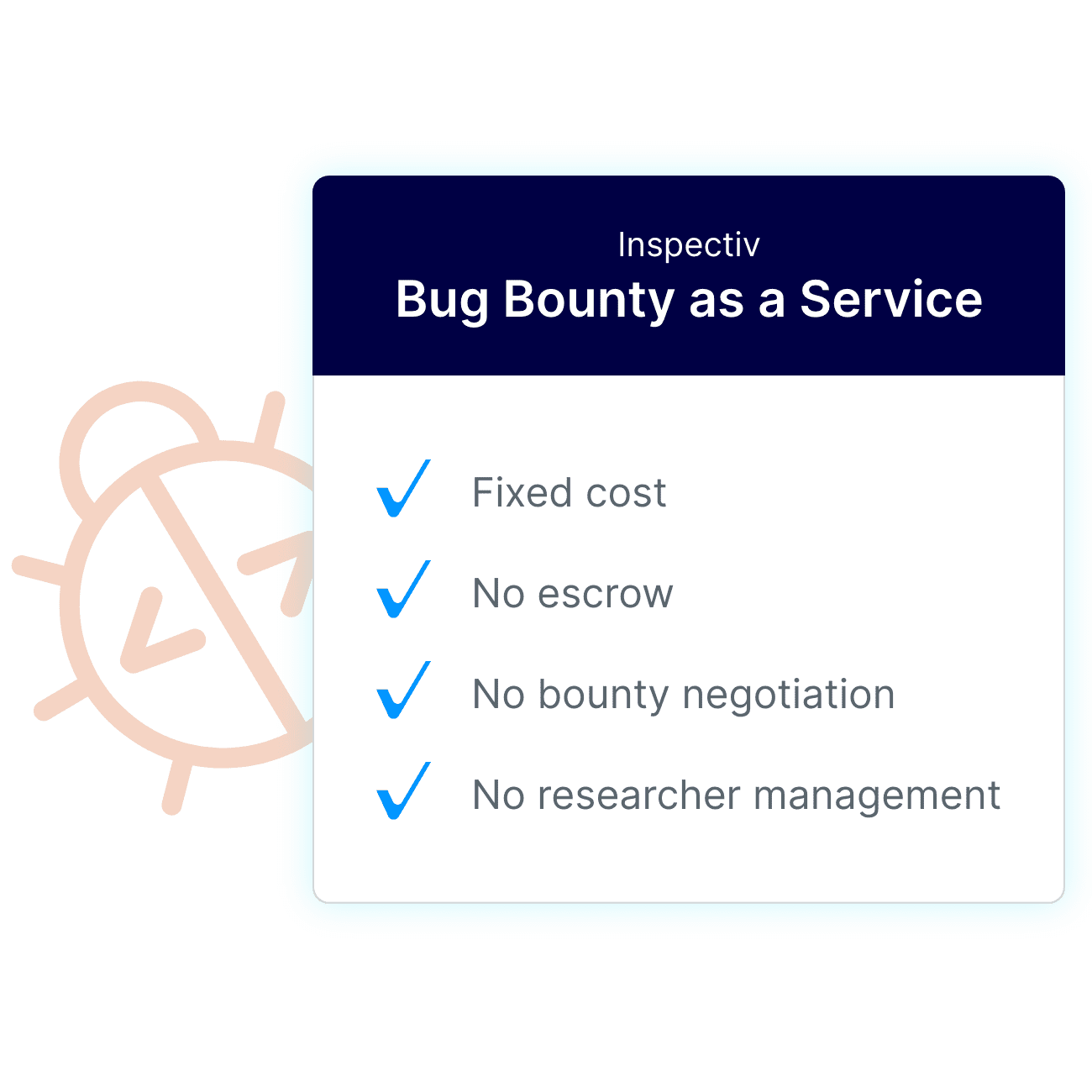
Bug Bounty vs. Pentesting: What’s Right for You?
Pentesting provides point-in-time validation. Bug bounty programs extend your reach with ongoing vulnerability discovery. Together, they create a continuous security testing strategy that helps you meet compliance and reduce risk.

|

|
|
|---|---|---|
| Primary Benefit |
Continuous Risk Reduction; Removal of Complex Security Vulnerabilities |
Compliance-Driven Security Testing |
| Testing Approach |
Grey Box + Black Box testing; only vulnerabilities reported |
Methodology Driven |
| Timing | Continuous | Time-Boxed |
| Testers | Researcher Community | Internal Security Team |
| Scope |
Web & Mobile Applications; APIs |
Active Directory; Cloud Security Embedded Softwares & IoT External & Internal Network Testing Red Team Assumed Breach Web & Mobile Applications; Web Infrastructure; APIs Wireless Assessments (incl’d Rogue Network Detection) |
|
Vulnerability Discovery |
Yes | Yes |

Removal of Complex Security Vulnerabilities
only vulnerabilities reported
APIs
Discovery

Embedded Softwares & IoT
External & Internal Network Testing
Red Team Assumed Breach
Web & Mobile Applications; Web Infrastructure; APIs
Wireless Assessments (incl’d Rogue Network Detection)
Discovery
Want full coverage? Bundle your Bug Bounty Program with Pentesting as a Service (PtaaS).
Ready to Launch Your Bug Bounty Program with Inspectiv?
Get a personalized demo
Discover how Inspectiv makes it easier to find, prioritize, and remediate critical vulnerabilities. Schedule your personalized demo to see how our platform streamlines security testing, reduces risk, and supports compliance all in one powerful solution.

